Desired State Configuration is a big part of most 2012 R2 certification tests; get an understanding from these 5 videos.
I have tried to arrange these in order; if you watch them in order, you should have a good basic understanding of DSC. It’s a very useful capability. The first two are approximately 1 hour each. DSC can do PUSH or PULL. Push would normally be ad hoc, test, or small needs. Most normal production use would be PULL.
Free eBook from Powershell.org The DSC Book
Time = 1:09
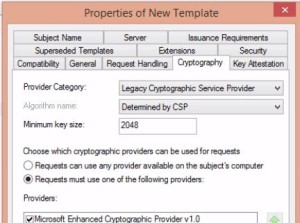
Description; Targeted somewhat to developers; or with a dev mindset. Give a good overview of the design, deployment and possible uses. Lots of groundwork explanation. .MOF (Managed Object Format) file creation and use. This is a classroom recording, so there is some live Q & A.
![]() VIDEO 2 – DSC is the ENDGAME for PowerShell
VIDEO 2 – DSC is the ENDGAME for PowerShell
Time = 1:04
Description; Windows PowerShell 4.0 introduces Desired State Configuration (DSC), and it’s time to put it to use. With DSC, you declaratively tell computers what you want them to look like, and how you want them to be configured, and let DSC make it happen and KEEP that configuration enforced. In this session, you not only see how DSC works, but you will be introduced to custom resource development, letting you start teaching; DSC how to configure internal applications, databases, and other infrastructure elements.
![]() VIDEO 3 – More hands on and examples
VIDEO 3 – More hands on and examples
Time = 1:17
Description; Are you paying attention to DevOps? Adoption of DevOps practices can greatly improve your company’s deployment efficiency. PowerShell Desired State Configuration (DSC) helps teams take the management of their Windows-based infrastructure into the DevOps space by capturing their infrastructure as code. The declarative PowerShell model enables autonomous, idempotent, and transparent configuration and deployment of Windows infrastructure and components. Capturing infrastructure as code is not only a means to manage what they have, at scale and speed, it is also a way to decouple the complexity of their existing environment in order to facilitate a migration to the cloud. Come see how DSC works and how you can use it to make configuration of internal applications, databases, and other infrastructure elements more efficient.
VIDEO 4 – Use Powershell DSC to install SQL Server
Time = :14
Description; I briefly show how powershell DSC can be used to configure and deploy a brand new SQL Server installation.